SOLVED PAPER OF HSST-COMPUTER SCIENCE/COMPUTER APPLICATION-HSST(JUNIOR & SENIOR) KERALA HIGHER SECONDARY EDUCATION EXAM HELD ON 19-09-2012.
[QUESTION PAPER CODE -143/2012.]
1) A document preparation software:
LATEX.
2) A technique in which system resources are shared among multiple users:
Multiplexing.
3) Interaction modelling cannot be done using:
State Diagrams.
4) The number of bits that can be transmitted over a network in a certain period of time.
Bandwidth.
5) Which of these is not a mark up language?
(A) HTML (B) XML (C) SGML (D) XGML.
Ans: XGML.
6) A network topology that combines features of linear bus and star topology?
Tree.
7) If language L={0,1}*, then the reversed language LR =
(0, 1}*
8) In Linux, the subdirectory that contains system configuration files including user passwords:
/etc.
9) SQL command to delete a column from an existing table:
Alter table.
10) A technique not associated with data mining:
Dimensionality Modelling.
11) Memory bank experiencing too much contention from processor:
Thrash.
12) T he number of nodes in a complete binary tree of height n:
2 n+1 -1
13) The science and art of breaking ciphers:
Steganography.
14) A raster scan display system with 24 bits per pixel and a screen resolution of 1024x 1024 requires a frame buffer of size:
3 Mega bytes.
15) Not a parallel programming language:
A)C* B) Sequent C C)n Cube C D)C++
Ans: C++
16) Process of mapping a network interface IP address to its hardware address:
ARP
17) For the following sample database table staff:
The SQL query: SELECT COUNT (Staff no) AS mycount, SUM(Salary) AS mysum FROM Staff
WHERE Designation=’Manager’
returns the result.
Ans: mycount=2, mysal=98000.
18) Linux partitions are credited using the file system:
(A) FAT B)FAT32 C) EXT3 D)NTFS
Ans: EXT 3
19) The local area network technology used in Ethernet
A)CSMA B)CSMA/CD C)CSMA/CA D)ALOHA
Ans: CSMA/CD
20) Data abstractions means:
Ans: Putting together essential feature without including background details.
21) A hardware interface that allows for the connection of several peripheral devices to a single PCI board:
SCSI
22) If n represents the dimension of cube and k, the radix(no. of nodes along each dimensions) then the number of nodes N of a K-ary n –cube network is :
N=kn
23) The output generated by the following C program:
# include
Main ()
{
int v=3;
int * pv;
pv=&v;
*pv=0;
Printf(“ *pv=%d v=%d ”, * pv,v );
Ans: *pv=0, v=0.
24) A famous technique used in data ware housing:
OLAP.
25) The environment variable in Linux , that contain a list of directories the shell automatically recognizes:
$ PATH.
26) Not an Anti-virus software:
A) McAfee B) Norton C)AVG D)TROJAN
Ans: TROJAN.
27) The following IP address format refers to:
Ans: Class C addresses.
28) In C++ , a pointer that is automatically being passed to a member function during its invocation is :
this pointer.
29) With QBE, inserting records from one or more source tables into a single target table can be achieved by :
Append action query.
30) Not an example of a network debugging utility:
A) Ping B)nslookup C) Traceroute D) telnet
Ans: telnet.
31) A security protocol for personal emails:
PGP.
32) If an g are functions ,then f(n)=ø(g(n)) if :
f(n)=O(g(n)) and f(n)= Ω(g(n)).
33) Simplified form of the Boolean expression
is:
Ans:
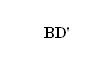
34) The post fix form of the expression (A+B)*C-D/E is: -
AB+C*DE/-
35) When a process is accessing shared modifiable data , the process is said to be in:
Critical section.
36) The first MPI function call made by every MPI Process is the call to :
MPI _ Init ( ).
37) Question Deleted.
38) Boundary value analysis is a method for :
Black box testing.
39) Dijkstra’s Banker’s algorithm is used for :
Deadlock Avoidance.
40) (P v q)≡ p q a famous law in logic known as :
De morgans’ law.
41) The language accepted by a push down automata:
Type 2.
42) In parallel algorithm design, the process of grouping tasks into larger tasks in order to improve performance :
Agglomeration.
43) A system call in Linux operating system to create a new child process, which is a copy of the parent process:
Fork.
44) A Preemptive type of process scheduling strategy:
A) Highest Response Ratio Next scheduling
B)Shortest job first out scheduling
C)First in first out scheduling
D)Shortest remaining time next scheduling
Ans: D)Shortest remaining time next scheduling.
45) The type of geometric transformation applied to an object for repositioning it along a straight line path from one location to another:
Translation.
46) Vignere cipher is a kind of:
Poly alphabetic cipher.
47) Recursive Descent parsers are a type of :
L L parsers.
48) The approach used for requirements elicitation in software design and development process:
A)View points B)Interview C)Use-Cases D)All of these
Ans: D)All of these.
49) The output generated by the following C program:
# include
int Update (int x)
{
static int y =10;
y + = x;
return(y);
}
main ()
{
int a, count;
for (count=0; count <3 br="" count="">
{
a = Update (count);
printf (“ % d”, a);
}
}
Ans: 10 11 13.
50) Area on earth where signals of a satellite can be received:
Foot- print.
51) Question Deleted.
52) A networking devices used to connect similar types of LANs:
Bridge.
53) A SIM card contain:
A) Personal identification number
B)International mobile subscriber identity
C)Authentication key
D)All of these
Ans: D)All of these.
54) In the given tree, in what order does the vertices are processed if in-order traversal is used:
Ans:CBEDAFGIHJ.
55) IC 74 LS 138 is a:
Decoder.
56) Binary search algorithm employs the strategy of :
Divide and Conquer Technique.
57) Dangling – else ambiguity can be eliminated by:
Matching else with nearest unmatched if.
58) Among the following , a representation that can be used for designing a system as a collection of procedures or modules:
A)Data flow diagrams B)Activity chart C)Flow chart D)E R Modelling
Ans: Data flow diagrams.
59) In C++, the following statements causes:
# include
int main()
{
int x = 10, y =5;
int * p = & x;
int * q = & y;
p = q;
delete (p);
return (0);
}
(A) p-a dangling reference (B) q-a dangling reference
(C) Both p and q as dangling reference. (D) None of these.
Ans: None of these.
60) Conversion from one data type to another data type, inserted automatically by a programming language:
Coercion.
61) The process of testing individual components in a software:
Unit testing.
62) In C++, the operator which cannot be overloaded:
A)Bitwise & operator B)Assignment operator C)== Operator D): : Operator
Ans: D): : Operator.
63) A solution to external fragmentation:
Compaction.
64) A type of inheritance in which the property of one class is inherited by more than one class:
Hierarchical inheritance.
65) The worst case time complexity of merge sort algorithm for input size n:
θ(n log n).
66) Question Deleted.
67) If a variable is declared as register type , then the operator that cannot be applied to it:Ans: Unary &.
68) Question Deleted.
69) What would be the output of the following C program.
# include
main ()
{
int x = 1 ;
while (x < = 1);
{
printf (“Good Morning”);
-- x;
}
}
(A) Good Morning (B) Good Morning infinite times
(C) Blank Display (D) Syntax Error.
Ans: Syntax Error.
70) In a compiler the task of scanning the source code, to recognize and classify various elements is known as:
Lexical Analysis.
71) Time Complexity of Prim’s minimum spanning tree algorithm is:
ø(n²).
72) A fact in prolog is a special case of a :
Rule.
73) Grammars that can be translated to DFAs:
Right Linear Grammar.
74) An example of a compiler-compiler is :
YACC.
75) A relation R on a set X is said to be a partial ordering if R is:
Reflexive, Anti-Symmetric ,Transitive.
76) What would be the output of the following C program.
# include
main ()
{
int i, x =1, y =1, z =0;
printf(“ % d % d”, x, y );
for (i=0, i < 3 ; i + +)
{
x + y = z;
printf (“ % d ”, z );
x = y;
y =z;
}
(A) 1 1 2 3 5 (B)1 1 1 1 1 (C) 1 1 0 0 0 (D) Syntax error.
Ans: Syntax Error.
77) Let V1={A,B,C} and V2={P, Q}, then the graph below is a :
Bipartite Graph.
78) Natural objects can be realistically modeled using:
Fractal Geometry.
79) Not a storage placement strategy for an incoming program/data:
Average Fit.
80) An attribute or set of attributes within one relation that matches the candidate key of some (possibly the same) relation:
Foreign Key.
81) A subset of data in a warehouse in the form of summary data, related to a particular department of business function:
Data Marts.
82) In an IP packet, header checksum computes:
1’s complement sum of 16 bit words in the header without data field.
83) A TCP server must prepare to accept a connection attempt from a TCP client by calling the function:
listen().
84) Not a Bernstein’s condition for two processes P1 and P2 executing in parallel on input set I1 and I2, producing output set 0 1 and 0 2 respectively.
I1∩I 2= Φ
85) The normalization of I N F relations to 2NF involves:
Removal of partial dependencies.
86) The technique used for dimensionality reduction of original data:
(A) Discrete Wavelet transform (B) Principal Component Analysis
(C) Both (A) and (B) (D) Neither (A) nor (B).
87) Question Deleted.
88) An objective measure of pattern interestingness in data mining:
(A) Support rule (B) Confidence rule
(C) Both (A) and (B) (D) Neither (A) nor (B).
Ans: Both (A) and (B).
89) DHCP stands for:
Dynamic Host Configuration Protocol.
90) A static member function can have access to:
Static members in the same class.
91) Hidden terminals in a wireless network may cause:
Collisions.
92) IC 80287 is :
Co-processor.
93) The maximum size of main memory of a computer is determined by:
Address Bus.
94) In computer terminology, POST stands for:
Power on Self Test.
95) SaaS is a popular term in the field of :
Cloud Computing.
96) Not an assembler directive
(A) XCHG (B) ASSUME (C) SHORT (D) DB
Ans: XCHG.
97) In a CDMA system, a code for a certain system should have:
(A) Good auto correlation with other codes.
(B) Orthogonality to other codes
(C) High standard deviation.
(D) Both (A) and (B).
Ans: Both (A) and (B).
98) 1 Kilo Bytes refers to :
1024 Bytes.
99) Tuple in a relational algebra refers to :
Row.
100) A ternary operator in C++
(A) ?: (B) I I (C) : : (D) . *
Ans: ? :






